Nakamoto ResearchCommunication language |
Version | v0.3.4 | |
|---|---|---|---|
| Updated | |||
| Author | obxium | License | BY-NC-ND |
This content is about communication language, and certain discovered nuances found in the communications of Satoshi Nakamoto. The communications are the constituents of a corpus the author is building.
Many researchers note peculiarities in Nakamoto’s style of English usage. In particular, Nakamoto’s inconsistent use of British English. This section records some examples and supporting resources to consider.
If you analyze the text corpus, you’ll arrive at a few possibilities to explain the inconsistent language choices and lack of spell checking:
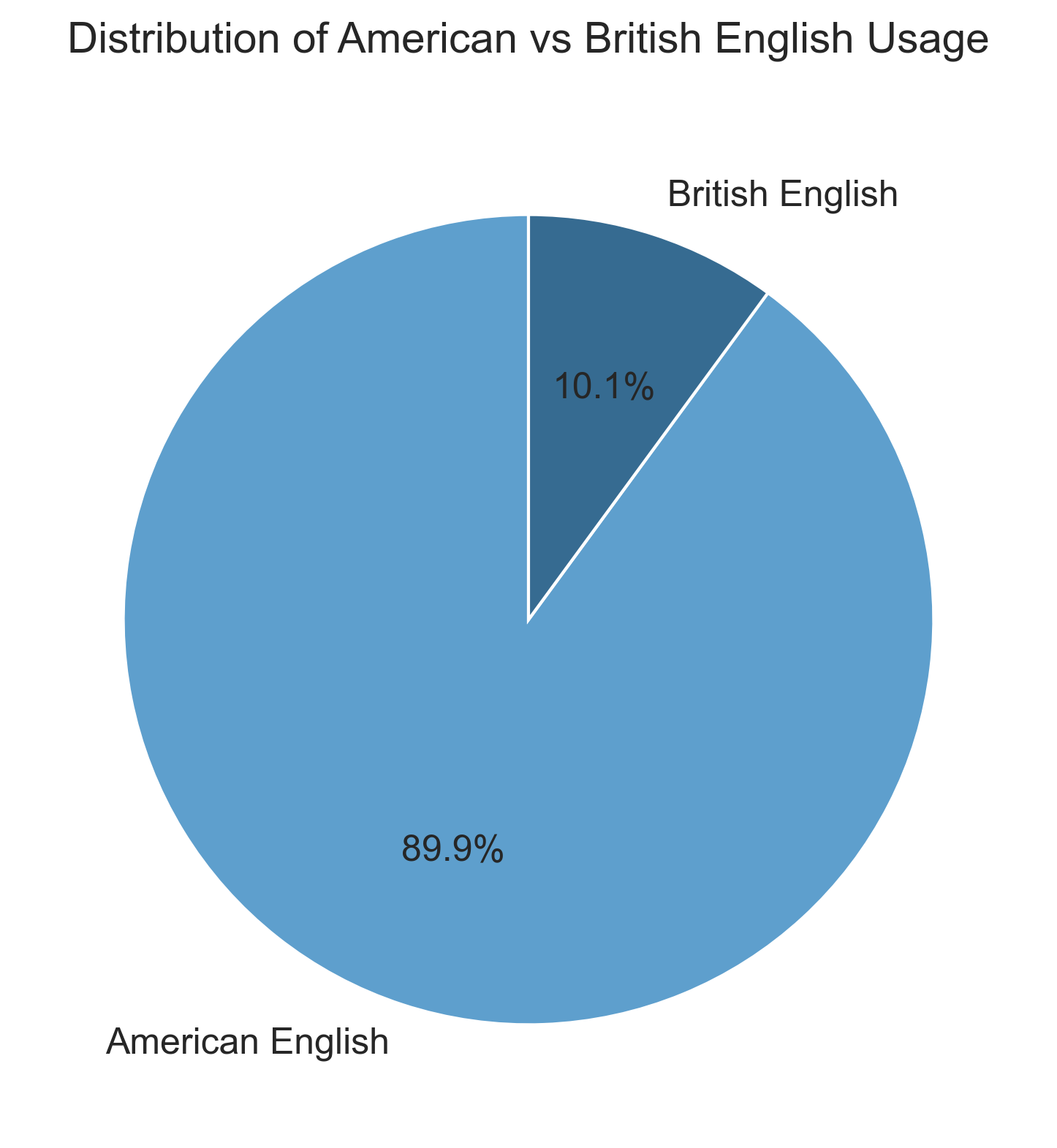
Here are statistics for an incomplete corpus of 81818 words with authorship attributed to Nakamoto.

Total American English variants found: 295
Total British English variants found: 33
Percentage split:
American English words found:
British English words found:
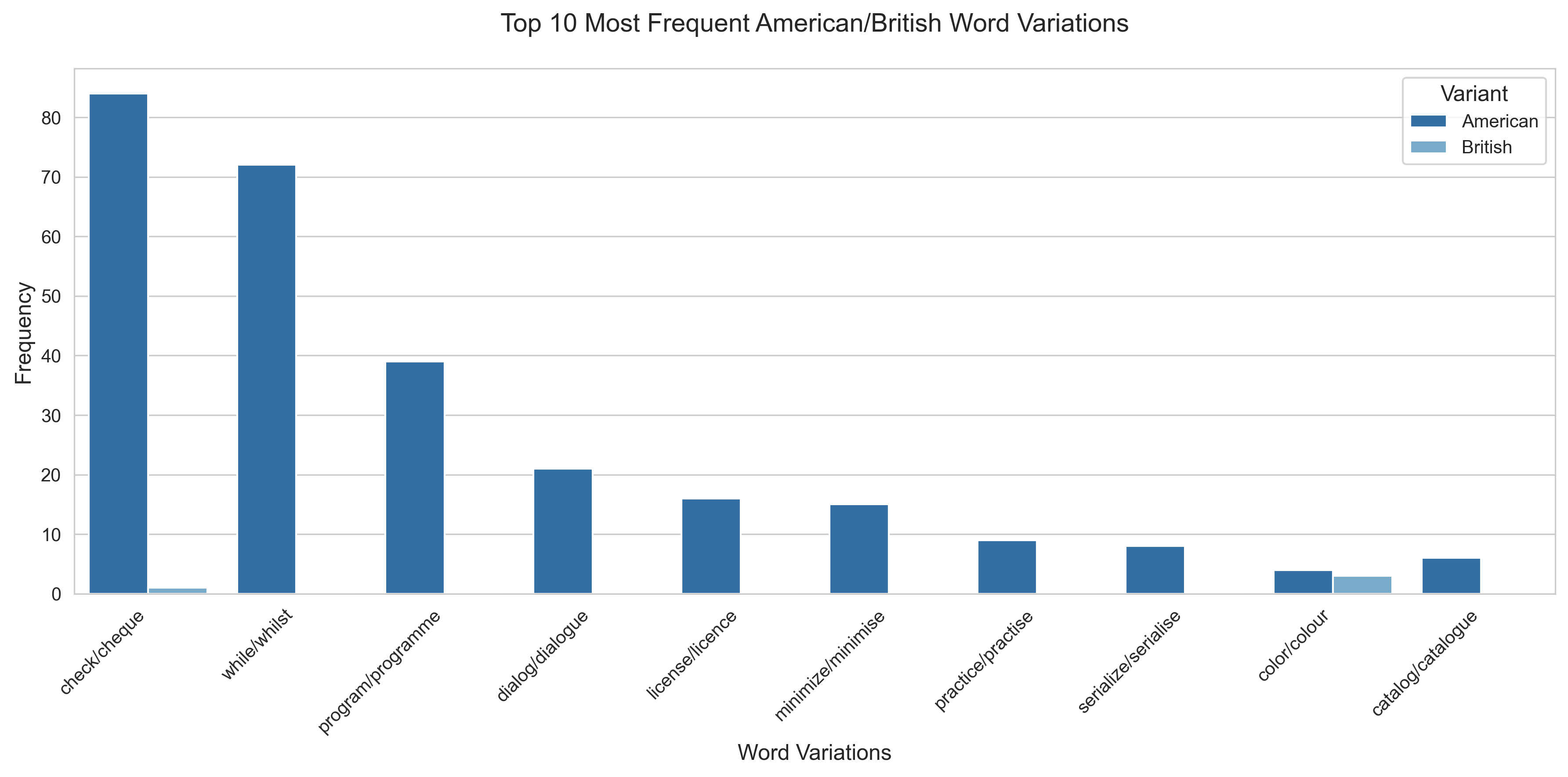
Here are the details on all the Nakamoto posts on the cryptography mailing list.
Total American English variants found: 12
Total British English variants found: 1
Percentage split:
American English words found:
British English words found: - neighbour: 1 (US: neighbor)
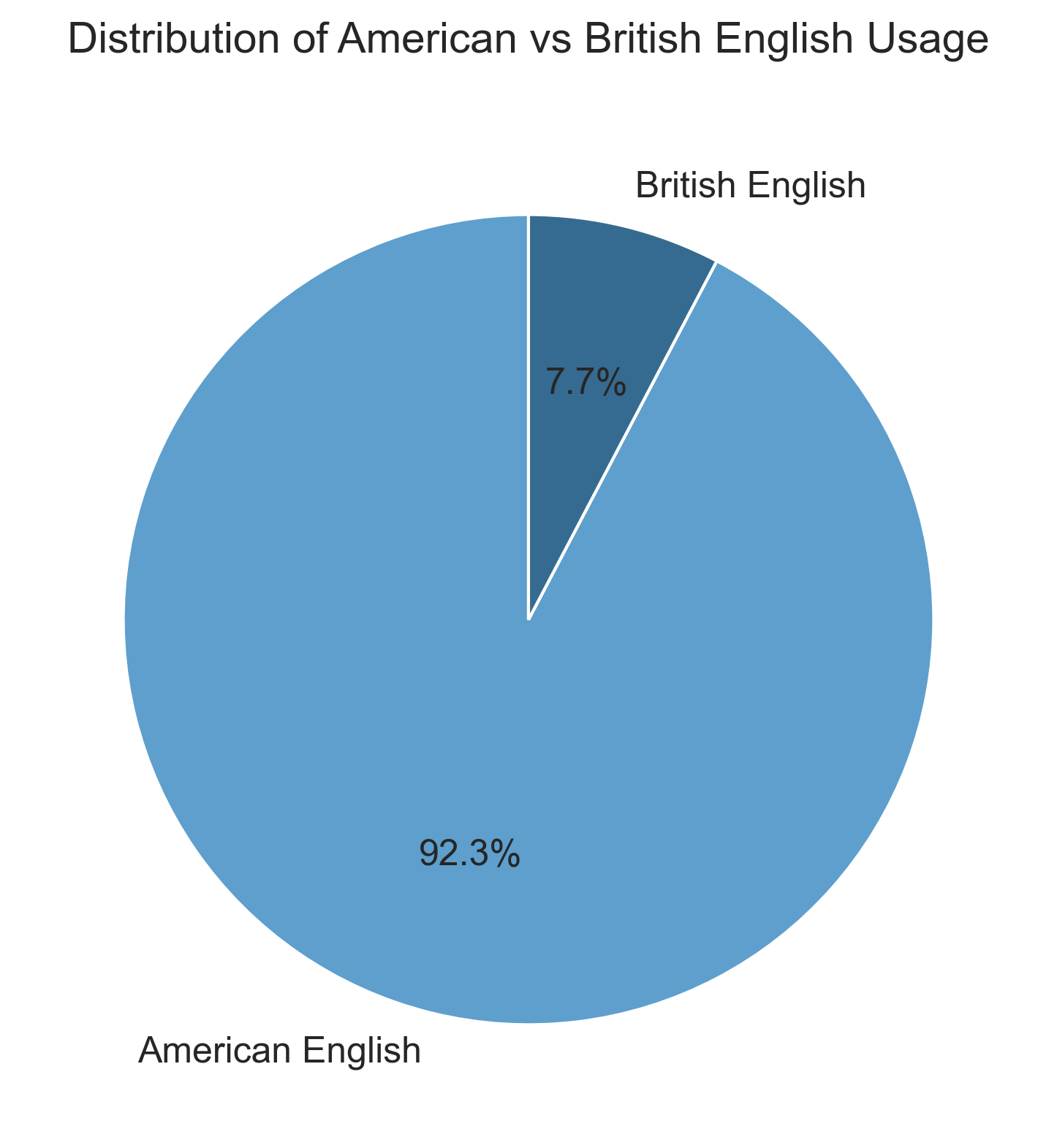
Here are the details on all the Nakamoto posts on the P2P Research forum.
Total American English variants found: 7
Total British English variants found: 0
Percentage split:
American English words found:
Here are the details on all the Nakamoto emails sent to Martti Malmi.
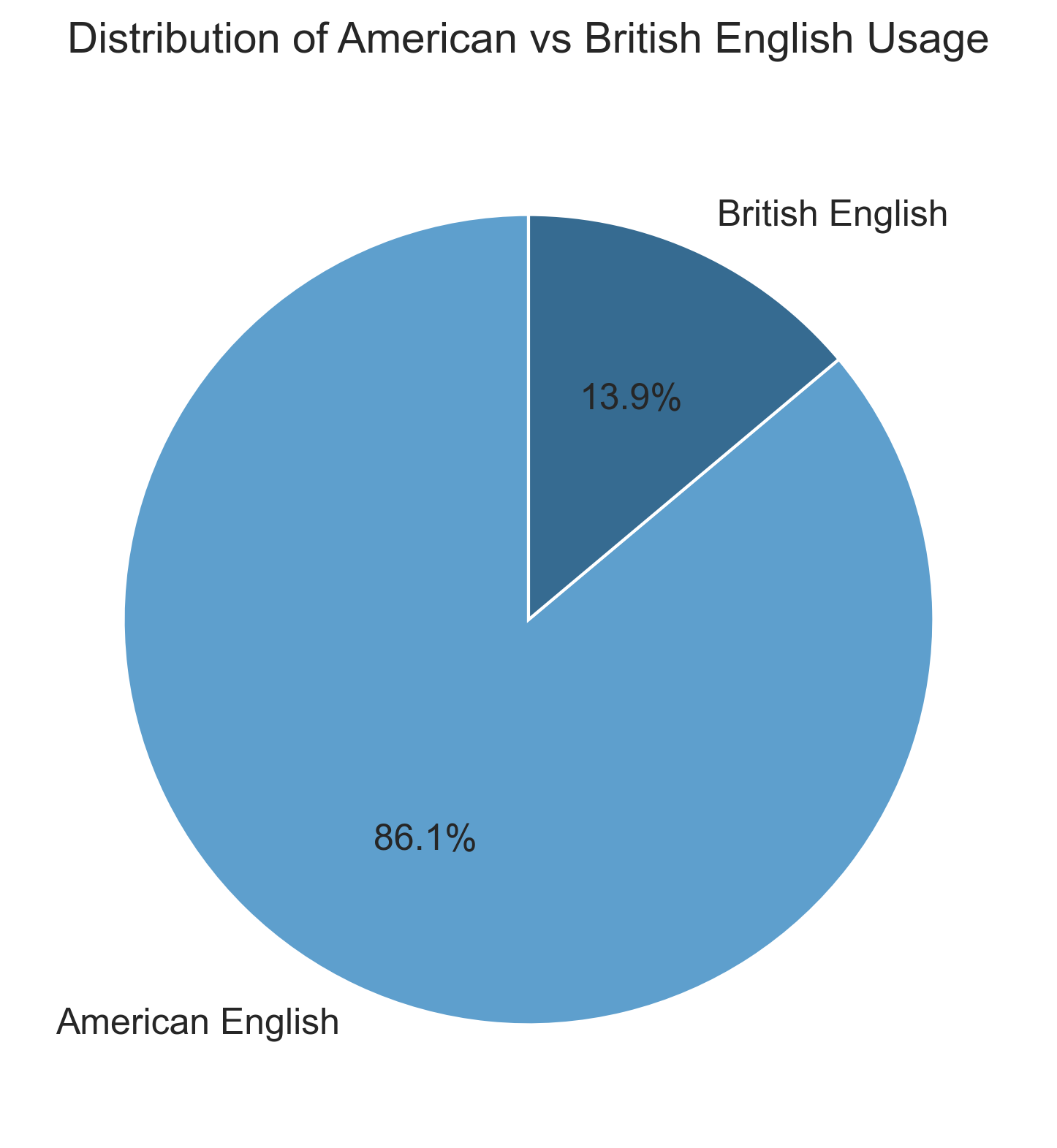
Total American English variants found: 62
Total British English variants found: 10
Percentage split:
American English words found:
British English words found:
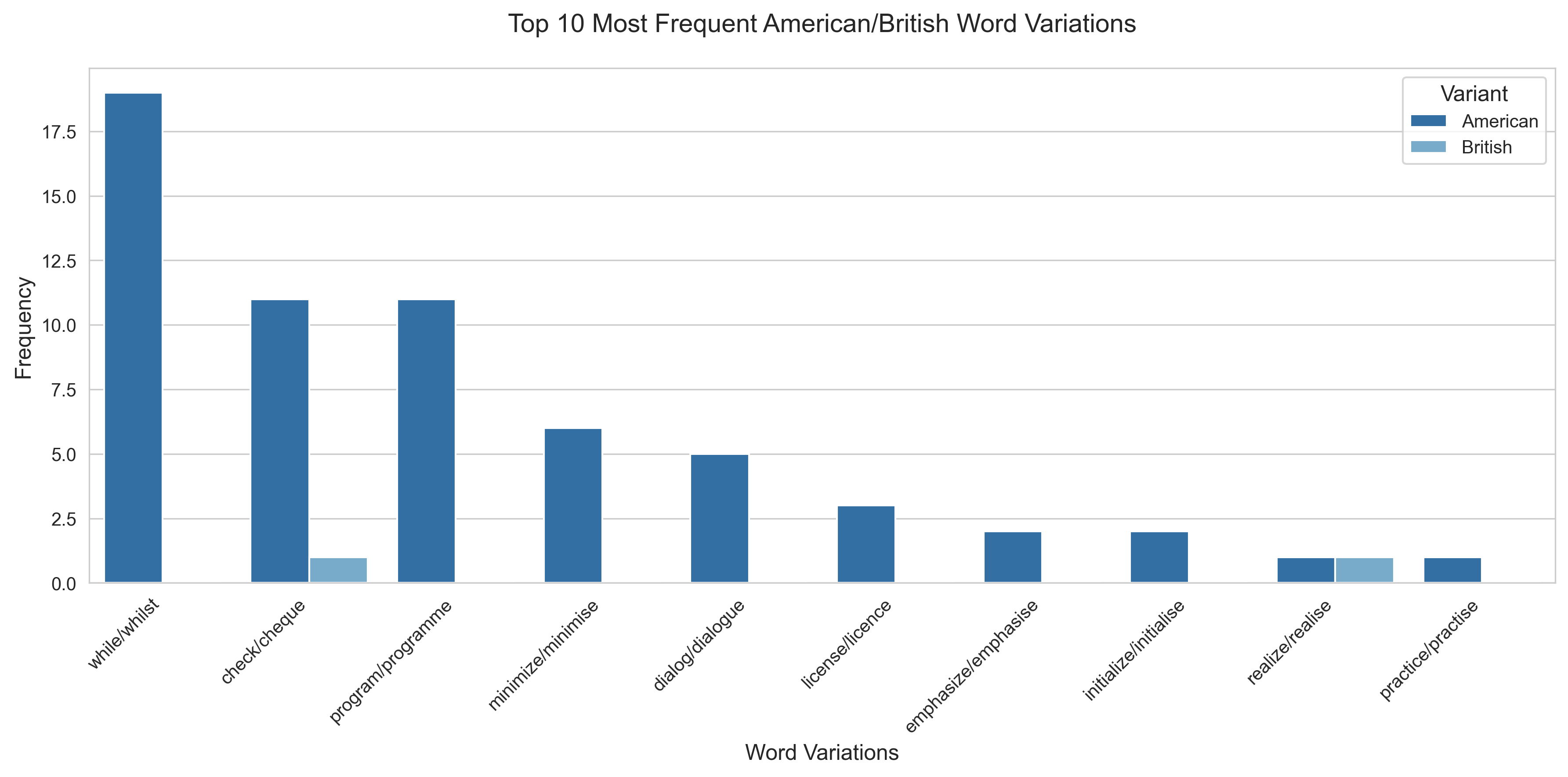
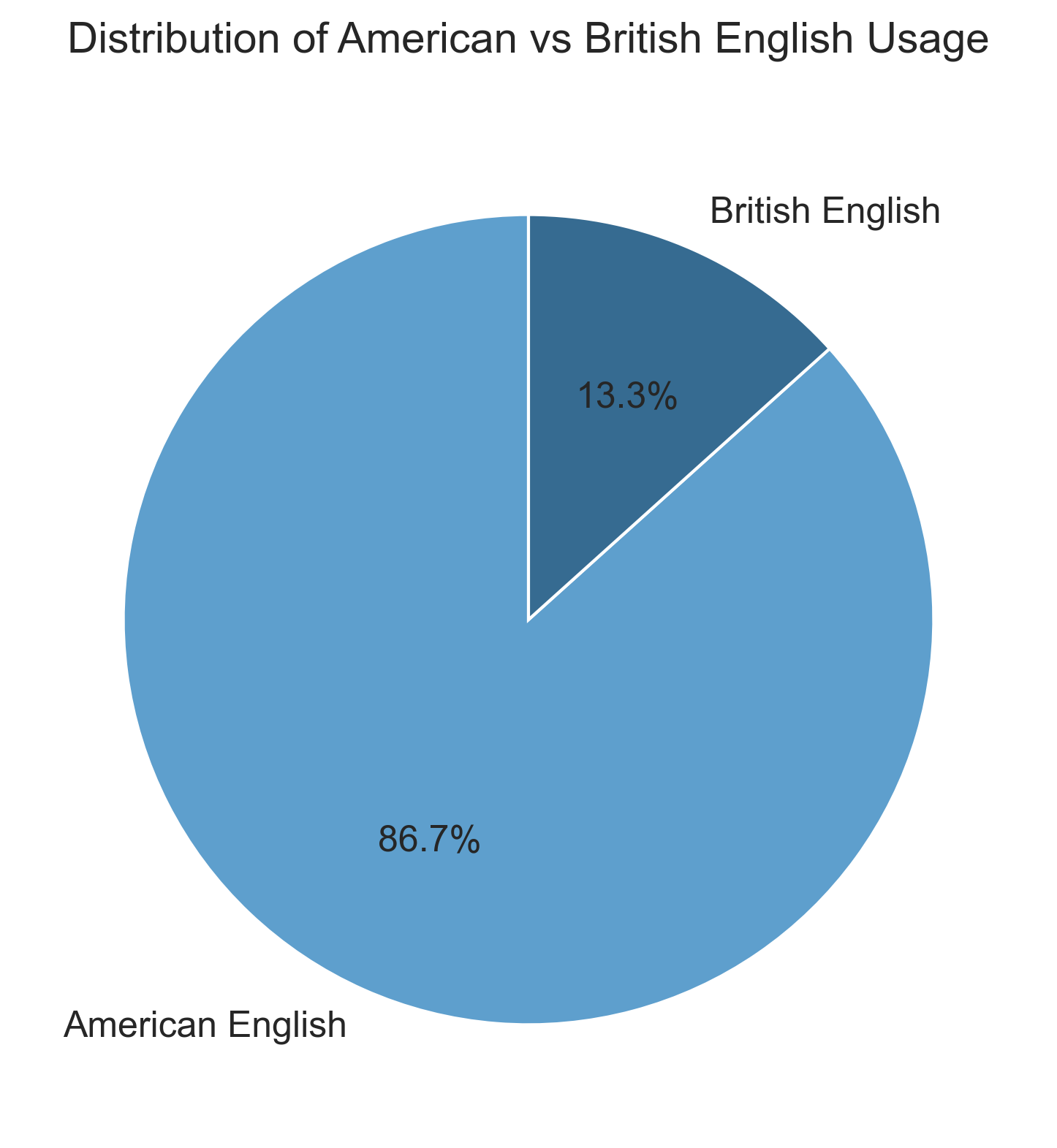
Here’s a breakdown of all comments in the Bitcoin version 0.1.0 source code.
Total American English variants found: 39
Total British English variants found: 6
Percentage split:
American English words found:
British English words found:
This section deals with particular colloquialism use across the corpus.
“Screw” is primarily a British-originated euphemism or slang term used for centuries with varying meanings. Common uses for screw include screwed, or screwed up or screwing up, which are slang for a bad situation or unfortunate circumstances.
Nakamoto uses 2 variations of screw with this slang meaning in
screwed up and screwing up within the Bitcoin
version 0.1.2 announcement:
Bitcoin v0.1.2 is now available for download.
See http://www.bitcoin.org for the download link.
All the problems I've been finding are in the code that
automatically finds and connects to other nodes, since I wasn't
able to test it in the wild until now. There are many more ways
for connections to get screwed up on the real Internet.
Bugs fixed:
- Fixed various problems that were making it hard for new nodes to
see other nodes to connect to.
- If you're behind a firewall, it could only receive one
connection, and the second connection would constantly disconnect
and reconnect.
These problems are kind of screwing up the network and will get
worse as more users arrive, so please make sure to upgrade.
Satoshi NakamotoLen Sassaman also used the term “screwed up” in a 2007 cypherpunks mailing list post.
From cypherpunks Wed Nov 07 19:37:22 2007
From: Len Sassaman <rabbi () abditum ! com>
Date: Wed, 07 Nov 2007 19:37:22 +0000
To: cypherpunks
Subject: Re: For those who missed it: Hushmail is pwnd
Message-Id: <Pine.LNX.4.58.0711071119460.19938 () thetis ! deor ! org>
X-MARC-Message: https://marc.info/?l=cypherpunks&m=119446646713988
On Wed, 7 Nov 2007, J.A. Terranson wrote:
> My guess is that Hushmail has had subpoenas before and had to develop
> and install a modified java applet which captures the passphrase when
> the user enters it. With that and the stored keys, it can decrypt all
> the stored communications.
I wouldn't be so certain -- getting subpoenas is no big deal for
companies. At Anonymizer, I answered lots of them. Most of the time, I
couldn't comply. (If you pay for your Anonymizer account with your credit
card, and the Feds want to know if you bought an Anonymizer account, well,
you screwed up. Otherwise, I told the guy on the phone the truth -- I had
nothing in my logs about that IP address, sir. And they went away,
quickly and without fuss, unlike when I've had to deal with the same
thing as a private remop.)
Of course, that was in 2003 and times have changed all around -- I don't
think Hushmail was handing out info to TLAs back then either.
Possibly, the problem here is Hushmail's move away from using its Java
applet as default. (It has two modes now -- securish and securisher, from
what I can tell, and the more secure "everything happens in the browser,
including all key operations" part is the optional step now. In the less
secure case, while I haven't analyzed it yet, I believe the keys in those
cases are being stored decryptable on the server. The passphrase is
almost certainly passed to the server.)
But, also, bear in mind that Hushmail has *always* allowed people to send
non-PGP messages, especially to non-Hushmail users. If one party was a
Hushmail user, and one party was not a PGP user, then PGP's not going to
be involved.
Regardless, boo for Hushmail for not disclosing that they were answering
subpoenas like this.
...
There *are* bigger forces at play, though. The "mutual assistance"
provisions of the Council of Europe cybercrime treaty are horrible, as are
these data retention laws. These are going to affect companies based in
any country signed to that treaty, including the US.
Hushmail, in the end, is relatively weak compared to other Cypherpunk
tools, and other ways of using them. The big They are trying to make those
other tools and uses illegal. Already we have people in the academic
privacy field scampering to appease their new masters, and trying to find
ways to do backdoored anonymity safely (are you kidding me? We haven't
even worked out the kinks with regular anonymity systems.) But in the end,
those are academics scared that their field is going to be made illegal,
and so their actions are understandable, if deplorable.
Likewise for whatever Hushmail may be doing.
A statement from the folks over there would be nice.
--Len.Hal Finney also used similar terms in posts made to the cypherpunks
mailing list in 2004, but the screw and
screwed here relates more to the usage that describes
getting a bad deal, ripped off, or rugged as the kids call it these
days.
From: Hal Finney <hal@rain.org>
Date: Sun, 13 Oct 1996 22:34:50 -0700 (PDT)
Subject: Re: Blinded Identities [was Re: exporting signatures only/CAPI]
...
Second, if the customer ever loses his credential, he is screwed.
He comes to you with some sob story about how his disk crashed and his
dog ate his backups, but you have no way of knowing if he actually lost
his credential, or if he is an abuser who got his credential cancelled.
Another problem is that groups of users can share credentials, so that
some hacker club can get a bunch, one for each of them, and then they
can all abuse your ISP, getting credentials cancelled, but able to keep
going as long as one is left.
...Date: Thu, 04 Nov 2004 23:01:15 +0000
Subject: RE: Your source code, for sale
"Tyler Durden" writes:
> So my newbie-style question is, is there an eGold that can be verified, but
> not accessed, until a 'release' code is sent?
>
> In other words, say I'm buying some hacker-ed code and pay in egold. I don't
> want them to be able to 'cash' the gold until I have the code. Meanwhile,
> they will want to see that the gold is at least "there", even if they can't
> cash it yet.
>
> Is there a way to send a 'release' to an eGold (or other) payment? Better
> yet, a double simultaneous release feature makes thing even more
> interesting.
I've been thinking about how to do this kind of thing with ecash.
One project I'm hoping to work on next year is a P2P gambling game (like
poker or something) using my rpow.net which is a sort of play-money ecash.
You'd like to be able to do bets and have some kind of reasonable
assurance that the other guy would pay up if he loses.
...
The problem is that if the source code you are purchasing is bogus,
or if the other side doesn't come through, you're screwed because you've
lost the value of the torn cash. The other side doesn't gain anything
by this fraud, but they harm you, and if they are malicious that might
be enough. And likewise you might be malicious and harm them by refusing
to give them your half of the coin even after you have received the goods.
Again, this doesn't benefit you, you're still out the money, but maybe
you like causing trouble.
...
Hal F.Originally a late 1800s phrase for smart alek, one who thinks they’re clever, or someone who is conceited, annoying, or brash.
You can find an instance of this term in the Bitcoin v0.1.0 source
file script.cpp at line 495:
// OP_NOTEQUAL is disabled because it would be too easy to say
// something like n != 1 and have some wiseguy pass in 1 with extra
// zero bytes after it (numerically, 0x01 == 0x0001 == 0x000001)These are certain peculiarities with how Nakamoto communicated, including mannerisms of English usage, key phrases, and quotations or sayings.
Nakamoto consistently uses a distinct style to represent an ordered list:
Here are some examples of Satoshi Nakamoto using this style:
Steps: 1) copy the current .org index.html to the new server exactly as-is. 2) switch the .org DNS entry. 3) keep working on the drupal site behind the scenes. 4) after google has had time to update its records, we can switch over to the drupal site.
and
For now, recommended steps: 1) Shut down. 2) Download knightmb’s blk files. (replace your blk0001.dat and blkindex.dat files) 3) Upgrade. 4) It should start out with less than 74000 blocks. Let it redownload the rest.
This ordered list style is a bit unconventional, and not found in the writings of Finney or Sassaman.
The quote appears in The Mythical Man-Month, which is a popular book among programmers.
You can find this quote in the Bitcoin v0.1.0 source file
util.cpp at line 320:
// "Never go to sea with two chronometers; take one or three."
// Our three chronometers are:
// - System clock
// - Median of other server's clocks
// - NTP servers
╭───────────────────────────────────────────────────────────────────────╮
│ ⚠ THIS CONTENT MAKES NO CLAIMS ABOUT THE IDENTITY OF SATOSHI NAKAMOTO │
╰───────────────────────────────────────────────────────────────────────╯